In the rapidly evolving world of the Internet of Things (IoT), security remains a top priority for both consumers and businesses.
As more devices become interconnected, the need for robust IoT Security Solutions has never been greater.

These solutions not only safeguard your devices from cyber threats but also ensure the privacy and integrity of the data transmitted between them.
In this article, we’ll explore the top IoT Security Solutions to consider in 2025.
We’ll delve into their features, use cases, and pricing details, providing you with a comprehensive guide to protect your devices in the ever-expanding IoT landscape.
Verdict on IoT Security Solutions
When it comes to securing IoT devices, having the right IoT Security Solutions is crucial.
With the increasing complexity of IoT networks, the tools you choose can significantly impact the safety and efficiency of your operations.
In 2025, these solutions are essential for protecting against the ever-evolving cyber threats targeting IoT devices.
From encryption tools to network monitoring software, each solution plays a vital role in ensuring your devices remain secure and your data private.
What Are IoT Security Solutions?
IoT Security Solutions are specialized tools and technologies designed to protect IoT devices and networks from cyber threats.

These solutions provide functionalities such as device authentication, data encryption, secure communication protocols, and network monitoring to safeguard against unauthorized access and data breaches.
They are essential for maintaining the integrity, confidentiality, and availability of the data transmitted across IoT networks.
| IoT Security Solutions | Best Features | User Experience and Reviews |
|---|---|---|
| Cisco IoT Threat Defense | – Network Segmentation – Anomaly Detection – Advanced Malware Protection – Integrated Firewall – Centralized Management | Widely used in healthcare and manufacturing sectors. Highly rated for reducing cyber threats and ensuring compliance. |
| Palo Alto Networks IoT Security | – Behavioral Analytics – Zero-Trust Security Model – Automated Policy Enforcement – Cloud Integration – Compliance Reporting | Favored by tech companies for proactive threat detection. Users appreciate its effectiveness in cloud-based environments. |
| Trend Micro IoT Security | – Easy Deployment – Threat Intelligence Integration – Device Management – Automated Updates – Scalability | Well-regarded by small businesses. Users find it easy to use with comprehensive protection at an affordable price. |
| Fortinet Security Fabric for IoT | – Unified Threat Management – Real-Time Monitoring – Automated Threat Response – Cloud-Based Management – High Scalability | Trusted by enterprises in energy and utilities. Praised for managing complex IoT networks with high security demands. |
| Kaspersky IoT Infrastructure Security | – Industrial-Grade Protection – Advanced Encryption – Real-Time Threat Detection – Compliance Management – Scalability | Widely trusted in the industrial sector. Known for its reliability in protecting critical infrastructure from threats. |
| Microsoft Azure IoT Security | – Integration with Azure IoT Hub – Real-Time Threat Detection – Compliance Management – Automated Security Updates – Scalability | Favored by businesses in the Azure ecosystem. Users highlight its seamless integration and enhanced IoT security. |
| IBM Watson IoT Platform Security | – AI-Powered Threat Detection – Secure Data Analytics – Integration with IBM Cloud – Compliance Tools – Customizable Security Policies | Widely used by organizations needing AI-driven security. Users appreciate its effectiveness in data-intensive industries like healthcare. |
Why Should You Consider IoT Security Solutions?
Choosing the right IoT Security Solutions is essential for several reasons:
- Device Protection: Safeguard IoT devices from unauthorized access and malicious attacks.
- Data Integrity: Ensure that the data transmitted between devices is accurate and has not been tampered with.
- Privacy: Protect sensitive information from being intercepted or accessed by unauthorized parties.
- Compliance: Meet regulatory requirements for data protection in IoT networks.
- Scalability: As your IoT network grows, these solutions can scale to accommodate more devices and increased data traffic.
Best Features for IoT Security Solutions in 2025
- Device Authentication: Ensures that only authorized devices can access your network.
- End-to-End Encryption: Protects data throughout its journey across the network.
- Real-Time Threat Detection: Monitors for and responds to potential threats as they occur.
- Secure Communication Protocols: Facilitates safe data exchange between devices.
- Network Monitoring: Provides visibility into network activity to detect anomalies.
Top 7 Recent IoT Security Solutions for 2025
1. Cisco IoT Threat Defense
Best For: Comprehensive network security.
Best Features: Integrated threat detection, robust encryption, and device visibility.
Product Descriptions: Cisco IoT Threat Defense is a powerful IoT security solutions offering a full suite of tools designed to protect IoT networks. It integrates seamlessly with existing Cisco security products, providing a holistic approach to safeguarding connected devices and their communications.
Ryan’s Advice: Ideal for businesses with extensive IoT networks that require reliable and scalable security measures.
Best Features for Cisco IoT Threat Defense:
- Network Segmentation: Isolates IoT devices from the main network to minimize potential attack vectors.
- Anomaly Detection: Identifies unusual patterns in network traffic to detect threats early.
- Advanced Malware Protection: Shields IoT devices from emerging malware threats.
- Integrated Firewall: Adds an extra layer of security for your IoT infrastructure.
- Centralized Management: Simplifies the management of IoT security across multiple devices.
User Experiences and Case Studies: Cisco IoT Threat Defense is widely used in industries such as healthcare and manufacturing, where secure IoT deployments are critical. Case studies highlight its effectiveness in reducing cyber threats and ensuring compliance with industry regulations.
Price Range:
- Small Businesses: Starting at $500/month.
- Enterprise: Custom pricing based on network size and requirements.
2. Palo Alto Networks IoT Security
Best For: Advanced threat prevention.
Best Features: Machine learning-based threat detection, seamless integration with cloud services.
Product Descriptions: Palo Alto Networks IoT Security is a leading IoT security solutions that leverages machine learning to protect IoT devices from unknown threats. This solution integrates with cloud services, making it ideal for organizations that rely heavily on cloud-based IoT infrastructure.
Ryan’s Advice: Best suited for businesses that require cutting-edge security for their IoT devices and networks, particularly those using cloud platforms.
Best Features for Palo Alto Networks IoT Security:
- Behavioral Analytics: Learns normal device behavior to identify and mitigate anomalies.
- Zero-Trust Security Model: Ensures no device is trusted by default, enhancing overall security.
- Automated Policy Enforcement: Simplifies the application of security policies across multiple devices.
- Cloud Integration: Seamless integration with major cloud platforms.
- Compliance Reporting: Helps businesses maintain compliance with regulatory standards.
User Experiences and Case Studies: This IoT security solutions is favored by tech companies for its proactive approach to threat detection and prevention. Case studies demonstrate its ability to reduce security incidents in cloud-based IoT environments.
Price Range:
- Cloud Service: Starting at $1,000/month.
- On-Premise: Custom pricing based on deployment scale and requirements.
3. Trend Micro IoT Security
Best For: Small to medium-sized enterprises.
Best Features: User-friendly interface, comprehensive threat intelligence.
Product Descriptions: Trend Micro IoT Security is an IoT security solutions that provides robust protection while being easy to deploy and manage. It is particularly suited for small and medium-sized businesses looking for effective security without the complexity.
Ryan’s Advice: Perfect for businesses seeking a cost-effective IoT security solutions that doesn’t compromise on features.
Best Features for Trend Micro IoT Security:
- Easy Deployment: Quick and straightforward setup process.
- Threat Intelligence Integration: Access to up-to-date threat data to protect against emerging threats.
- Device Management: Simplified management of multiple IoT devices from a single interface.
- Automated Updates: Ensures devices are protected with the latest security patches.
- Scalability: Can grow with your business as your IoT network expands.
User Experiences and Case Studies: Trend Micro IoT Security is well-regarded by small businesses for its ease of use and effective protection. Users appreciate the intuitive interface and the comprehensive security it provides at an affordable price.
Price Range:
- Basic Plan: $300/year.
- Advanced Plan: $600/year.
4. Fortinet Security Fabric for IoT
Best For: Comprehensive security across hybrid environments.
Best Features: Unified threat management, real-time monitoring, and automated responses.
Product Descriptions: Fortinet’s Security Fabric is an IoT security solutions that offers a broad range of security measures tailored for IoT devices, particularly in complex network environments. It integrates with Fortinet’s existing security products to provide a cohesive and powerful security framework.
Ryan’s Advice: Ideal for businesses operating in both physical and virtual environments that require a unified security approach.
Best Features for Fortinet Security Fabric:
- Unified Threat Management: Combines multiple security features into a single platform for easier management.
- Real-Time Monitoring: Continuously monitors IoT networks for potential threats.
- Automated Threat Response: Automatically mitigates threats as they are detected.
- Cloud-Based Management: Allows for easy management of IoT security across multiple sites and devices.
- High Scalability: Designed to support large enterprises with extensive IoT deployments.
User Experiences and Case Studies: Fortinet Security Fabric is trusted by enterprises in sectors such as energy and utilities, where security and reliability are critical. Case studies show its effectiveness in managing complex IoT networks with high security demands.
Price Range:
- Standard Package: $800/month.
- Enterprise Package: Custom pricing based on network complexity.
5. Kaspersky IoT Infrastructure Security
Best For: Industrial IoT applications.
Best Features: Industrial-grade security, robust encryption, and real-time threat detection.
Product Descriptions: Kaspersky IoT Infrastructure Security is a specialized IoT security solutions designed for industrial environments. It provides top-tier protection for critical infrastructure, ensuring that industrial IoT deployments remain secure and operational.
Ryan’s Advice: A must-have for businesses in the industrial sector where IoT devices are integral to operations.
Best Features for Kaspersky IoT Infrastructure Security:
- Industrial-Grade Protection: Specifically designed for the unique needs of industrial IoT applications.
- Advanced Encryption: Protects data at every stage, from collection to transmission.
- Real-Time Threat Detection: Constantly monitors for potential security breaches in industrial settings.
- Compliance Management: Assists in meeting industry-specific regulatory requirements.
- Scalability: Can support large industrial networks, making it suitable for extensive deployments.
User Experiences and Case Studies: Kaspersky’s IoT security solutions is widely trusted in the industrial sector for its reliability and effectiveness. Case studies highlight its success in protecting critical infrastructure from cyber threats.
Price Range:
- Small Installations: Starting at $1,200/year.
- Large Networks: Custom pricing based on the number of devices and network size.
6. Microsoft Azure IoT Security
Best For: Integration with Microsoft Azure IoT services.
Best Features: Seamless integration with Azure IoT Hub, comprehensive security management, and real-time threat detection.
Product Descriptions: Microsoft Azure IoT Security is a robust IoT security solutions that integrates directly with Azure IoT services, providing end-to-end security for IoT devices and networks. It leverages Microsoft’s extensive cloud infrastructure to offer scalable security solutions.
Ryan’s Advice: Ideal for organizations already using Azure IoT services, looking to streamline their security management within the Azure ecosystem.
Best Features for Microsoft Azure IoT Security:
- Integration with Azure IoT Hub: Provides seamless security management across Azure IoT devices.
- Real-Time Threat Detection: Continuously monitors for and responds to potential threats.
- Compliance Management: Helps ensure compliance with industry regulations using built-in tools.
- Automated Security Updates: Keeps devices protected with the latest security patches.
- Scalability: Easily scales with the growth of your IoT deployment.
User Experiences and Case Studies: Microsoft Azure IoT Security is favored by businesses that are heavily invested in the Azure ecosystem. Case studies show how it enhances security for IoT deployments in various industries, from manufacturing to retail.
Price Range:
- Free Tier: Basic security features included with Azure IoT Hub.
- Premium Tier: Custom pricing based on device count and service usage.
7. IBM Watson IoT Platform Security
Best For: AI-driven security for IoT devices.
Best Features: AI-powered threat detection, secure data analytics, and integration with IBM Cloud.
Product Descriptions: IBM Watson IoT Platform Security is an advanced IoT security solutions that leverages artificial intelligence to protect IoT devices. It integrates with IBM’s cloud services to provide a secure environment for IoT data and devices, making it ideal for businesses that require intelligent security solutions.
Ryan’s Advice: Best suited for organizations looking to harness the power of AI to enhance their IoT security posture.
Best Features for IBM Watson IoT Platform Security:
- AI-Powered Threat Detection: Uses machine learning to detect and respond to threats in real-time.
- Secure Data Analytics: Protects sensitive data as it is analyzed and processed.
- Integration with IBM Cloud: Seamlessly connects with IBM’s cloud services for enhanced security.
- Compliance Tools: Helps businesses meet various regulatory requirements through automated processes.
- Customizable Security Policies: Allows for the creation of tailored security policies for different IoT environments.
User Experiences and Case Studies: IBM Watson IoT Platform Security is widely used by organizations that need cutting-edge AI-driven security. Case studies illustrate its effectiveness in industries such as healthcare, where data security is paramount.
Price Range:
- Basic Plan: Starting at $1,000/month.
- Enterprise Plan: Custom pricing based on AI usage and data volume.
Current Trends in IoT Security

Latest Trends in IoT Security for 2025
As the adoption of IoT devices continues to grow, so does the complexity and scope of securing these networks.
In 2025, several key trends are shaping the landscape of IoT security solutions, each driven by the need to protect increasingly sophisticated and widespread IoT deployments.
AI-Driven Threat Detection
One of the most significant trends in IoT security is the integration of artificial intelligence (AI) into security frameworks.
AI-driven threat detection allows IoT security solutions to analyze vast amounts of data generated by IoT devices, identifying patterns and anomalies that could indicate a security breach.
This proactive approach enables real-time responses to threats, significantly reducing the potential damage from cyberattacks.
Edge Computing Security
With the rise of edge computing, data processing is increasingly being done closer to the source of data (i.e., IoT devices) rather than relying on centralized cloud servers.
This shift has significant implications for IoT security solutions. Edge computing requires localized security measures that can protect data at the edge while ensuring that the overall network remains secure.
IoT security solutions are evolving to include robust encryption, secure communication protocols, and real-time threat detection at the edge, making the entire network more resilient.
Blockchain Integration in IoT Security
Blockchain technology is being increasingly integrated into IoT security solutions to provide immutable and transparent records of transactions and device interactions.
By using blockchain, IoT security solutions can ensure that data integrity is maintained across the network, making it nearly impossible for unauthorized parties to alter or tamper with data.
This is particularly valuable in industries like supply chain management, where the authenticity and traceability of data are critical.
Zero-Trust Security Models
The concept of zero-trust security has gained substantial traction in 2025, particularly within IoT networks.
Unlike traditional security models that trust devices within the network perimeter, zero-trust security models assume that every device, whether inside or outside the network, could be a potential threat.
IoT security solutions are increasingly adopting zero-trust principles, requiring continuous verification of device identities, strict access controls, and the monitoring of all network activity to ensure that only authorized devices can interact within the IoT ecosystem.
Challenges in IoT Security
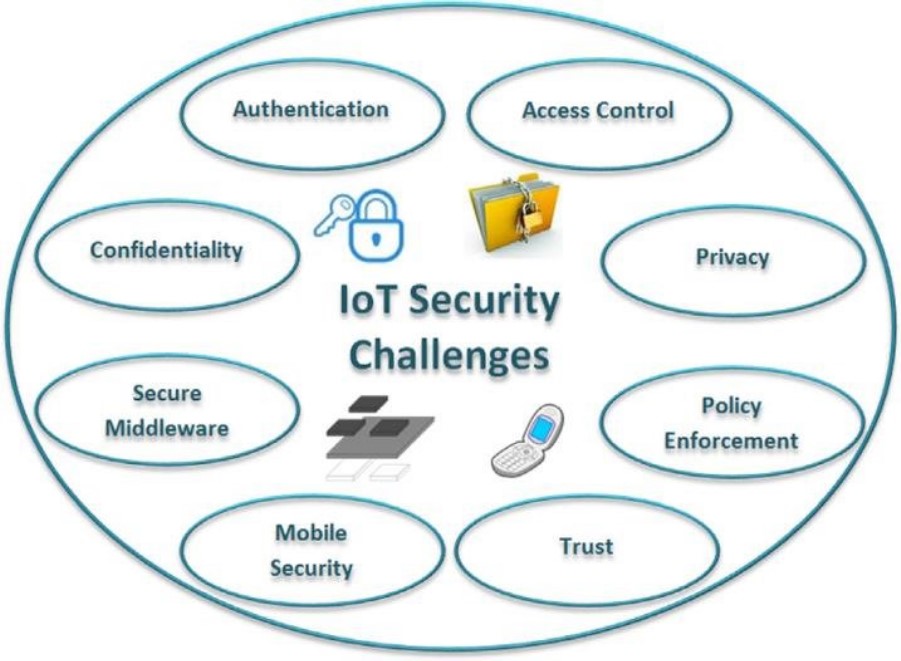
Common Security Challenges Faced by IoT Networks
The rapid expansion of IoT networks has brought numerous security challenges to the forefront.
IoT security solutions must address these challenges to ensure the safe and reliable operation of connected devices.
Device Vulnerabilities
One of the most pressing challenges in IoT security is the inherent vulnerability of many IoT devices.
These devices often have limited processing power, making it difficult to implement advanced security measures such as encryption and real-time threat detection.
Additionally, many IoT devices are designed with convenience in mind, often at the expense of security, leaving them susceptible to exploitation by malicious actors.
Lack of Standardization
The lack of standardization in IoT device manufacturing and communication protocols poses a significant challenge for IoT security solutions.
Without consistent standards, it becomes difficult to implement uniform security measures across different devices and networks.
This fragmentation can lead to security gaps, where some devices are inadequately protected, making them easy targets for cyberattacks.
Data Privacy Concerns
With the vast amount of data generated by IoT devices, ensuring data privacy is a major challenge.
IoT security solutions must not only protect data from unauthorized access but also ensure that data is processed and stored in compliance with privacy regulations.
This is particularly challenging in environments where IoT devices are constantly communicating and exchanging data, often across multiple jurisdictions with differing privacy laws.
Impact on Consumers and Businesses
These challenges impact both consumers and businesses alike. For consumers, the potential for data breaches and privacy violations can lead to a loss of trust in IoT devices, limiting their adoption.
For businesses, the consequences can be even more severe, including financial losses, legal liabilities, and reputational damage.
Therefore, it is critical for IoT security solutions to address these challenges effectively to maintain the integrity and trustworthiness of IoT networks.
Best Practices for Implementing IoT Security

Actionable Tips for Securing IoT Devices and Networks
Implementing IoT security solutions effectively requires a combination of best practices that ensure the safety and reliability of IoT devices and networks.
Device Authentication
Ensuring that only authorized devices can access your IoT network is crucial.
IoT security solutions should include robust device authentication protocols that verify the identity of each device before it can connect to the network.
This prevents unauthorized devices from gaining access and potentially compromising the entire system.
Encryption
Encryption is a fundamental component of IoT security solutions.
By encrypting data both at rest and in transit, you can protect sensitive information from being intercepted or tampered with.
Ensure that your IoT security solutions include strong encryption standards, such as AES-256, to safeguard your data.
Regular Updates
Keeping IoT devices and security solutions up to date is essential for protecting against new and evolving threats.
Implement a regular update schedule that includes firmware, software, and security patches to address vulnerabilities as they arise.
Network Segmentation
Segmenting your IoT network can help contain potential breaches by isolating critical devices and data from less secure areas of the network.
IoT security solutions should support network segmentation, allowing you to create virtual networks that restrict access to sensitive information.
Ongoing Monitoring and Threat Detection
Continuous monitoring of your IoT network is vital for detecting and responding to threats in real time.
IoT security solutions with advanced threat detection capabilities, such as AI-driven analytics, can help identify anomalies and prevent security incidents before they cause significant damage.
Case Studies and Success Stories
Real-World Examples of Successful IoT Security Implementations
Securing a Smart City with Cisco IoT Threat Defense
A leading smart city project integrated Cisco IoT Threat Defense to secure its vast network of connected devices, ranging from traffic sensors to public safety cameras.
The solution provided real-time threat detection and network segmentation, ensuring the city’s IoT infrastructure remained secure and operational.
- Challenges: Securing a large-scale, public IoT network with diverse devices.
- Solution: Cisco IoT Threat Defense provided comprehensive security, reducing the risk of cyberattacks.
- Outcome: The city achieved enhanced security and reliability, maintaining public trust in its IoT systems.
Industrial IoT Security with Kaspersky IoT Infrastructure Security
A major manufacturing company deployed Kaspersky IoT Infrastructure Security to protect its industrial IoT devices, which are critical to its production processes.
The solution’s industrial-grade protection and real-time threat detection ensured that the company’s operations continued without disruption.
- Challenges: Protecting industrial IoT devices from cyber threats that could halt production.
- Solution: Kaspersky IoT Infrastructure Security offered robust protection tailored for industrial environments.
- Outcome: The company successfully mitigated potential security threats, ensuring continuous production and avoiding costly downtime.
Future of IoT Security

Predictions for the Future of IoT Security
As IoT continues to evolve, so too will the threats and security measures designed to combat them.
Here are some predictions for the future of IoT security solutions.
Integration of Quantum Computing
Quantum computing holds the potential to revolutionize IoT security solutions.
With its immense computational power, quantum computing could break traditional encryption methods, necessitating the development of quantum-resistant algorithms.
Conversely, quantum computing could also enhance IoT security by enabling more advanced encryption techniques and faster threat detection.
Increased Regulatory Scrutiny
As IoT devices become more widespread, governments and regulatory bodies are likely to impose stricter security standards and compliance requirements.
Businesses will need to ensure that their IoT security solutions are robust enough to meet these new regulations, which may include mandatory encryption, regular security audits, and data privacy protections.
Growth of AI-Driven Security
AI will continue to play a significant role in the future of IoT security solutions.
As AI technologies advance, they will become more adept at identifying and responding to complex threats, providing a higher level of security for IoT networks.
AI-driven security solutions will likely become the standard, offering automated threat detection, response, and continuous learning to adapt to new attack vectors.
Common Mistakes in IoT Security Implementation

Identifying and Avoiding Common IoT Security Pitfalls
Implementing IoT security solutions can be challenging, and many businesses make mistakes that leave their networks vulnerable. Here are some common mistakes and how to avoid them.
Neglecting to Update Devices Regularly
One of the most common mistakes is failing to regularly update IoT devices and security solutions. Outdated firmware and software can leave devices vulnerable to known threats.
To avoid this, implement a strict update policy and ensure that all devices are regularly patched and updated.
Overlooking Device Authentication
Many businesses fail to implement strong device authentication protocols, allowing unauthorized devices to access their networks.
Ensure that your IoT security solutions include robust authentication measures, such as multi-factor authentication, to prevent unauthorized access.
Inadequate Network Segmentation
Without proper network segmentation, a breach in one part of the network can spread to other areas, compromising the entire system.
Implement network segmentation as part of your IoT security strategy to isolate sensitive devices and data from less secure parts of the network.
Underestimating the Importance of Encryption
Some businesses neglect to encrypt data at every stage of its journey, leaving it exposed to interception and tampering.
Ensure that your IoT security solutions include strong encryption protocols to protect data both at rest and in transit.
FAQs on IoT Security Solutions
Answering Common Questions About IoT Security Solutions
Q: What are IoT security solutions? A: IoT security solutions are tools and technologies designed to protect IoT devices and networks from cyber threats. They include features such as device authentication, encryption, threat detection, and network segmentation.
Q: Why is IoT security important? A: IoT security is crucial because IoT devices often handle sensitive data and are integral to critical operations. Without proper security, these devices are vulnerable to cyberattacks, which can lead to data breaches, financial loss, and operational disruptions.
Q: What are the common challenges in IoT security? A: Common challenges include device vulnerabilities, lack of standardization, data privacy concerns, and the complexity of securing large, diverse IoT networks.
Q: How do IoT security solutions protect against threats? A: IoT security solutions protect against threats by implementing measures such as device authentication, encryption, real-time threat detection, and continuous monitoring to identify and respond to potential security incidents.
Q: Can IoT security solutions be integrated with existing IT security frameworks? A: Yes, many IoT security solutions are designed to integrate seamlessly with existing IT security frameworks, providing a unified approach to protecting both IoT and traditional IT environments.
Q: How do I choose the right IoT security solution for my business? A: When choosing an IoT security solution, consider factors such as the size and complexity of your IoT network, your industry-specific security requirements, your budget, and the level of support and scalability offered by the solution.
Q: What are the best practices for securing IoT devices? A: Best practices include implementing device authentication, encrypting data, keeping devices updated, segmenting the network, and continuously monitoring for threats.
